WOW. I am really proud. Apollo is ahead of the curve in SOOO many ways. Now mind you we're not at the apex of Gartner's Maturity Model which is Policy Based (and yes that is our new target) BUT...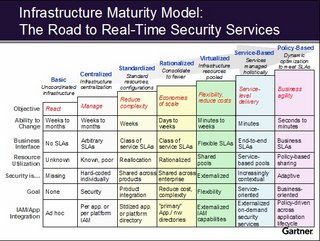
We're at the Virtualized stage, our objectives now are increasing business efficiency to reduce costs in labor intensive or time intensive business activities.
A whopping 73% of Gartner customers DON'T do automated user provisioning. Likewise, all the products we looked at have CRUDE interfaces, ill defined interactions, and are still half baked. Even Oracle, the best identity and access management suite on the market today is only a rebranded amalgam of their most recent acquisitions. It introduces yet another workflow technology, it has gaps in what it can and can't do, namely business roles and role governance. For that it recommends we leverage someone like Bridgestream, which has yet another web interface for business users to use in requesting business roles (apparently only IT users use Oracle Identity Manager to request IT only roles) and yet another workflow engine for our support teams to learn. Add to that the spartan and un-intuitive interfaces on both products, and we look like rock stars.
We are in fact rock stars, what we've done and in the time that we've done it is nothing short of miraculous. We're in the top 27% of Gartner customers for user provisioning and I'm quite sure we're even higher considering the periodic audits we've been doing for a full year this month. At the user round table I attended Thursday, I was ahead of all but one customer and even then we had features and maturity that they were only now starting to consider.
So, considering all of this, where do we go next? Well there are still significant gaps in our offerings, and most certainly, opportunities for growth. Here's the short list of things we're missing or needing to improve upon:
UI: what we've got in the CAP UI is extensible, robust in comparison, far easier to user and more elegant than anything we saw at the conference. But being the rock stars we are we cant settle for success. Let's take it to the next level, let's simplify the UI and make it clean. We'll engage the HCI team in order to get this done. Think of the good Web 2.0 designs we've seen like Google, Skype, Delicious, and you'll have an idea of what it is that we want to do.
On-boarding: We need to simplify the on-boarding process for all new users. CAP can still be the place we go for on-boarding contractors. But when we hire staff or convert contractors to staff we HAVE to vastly simplify and streamline that process. Users shouldnt have to go from HR to CAP to put in access requests. Likewise, we should be able to identify people as existing identities when we provision them so we dont end up with duplicates. Every vendor has this, so should we.
Default access levels: When we on-board people we should automatically grant them a default level of access based on a role. This access would include network access, email, and some combination of roles based on their job code and cost code.
Email access: Its not fully automated provisioning until we include email. This is #1. Enough said.
Role Management: We need a means of adding or removing roles within CAP, the identity management environment, and downstream in the applications. This is a larger, multi-year goal but one we should pursue nonetheless. We should include some manor of reporting all the roles and role mappings in the system as well as who has these roles and who is in violation of the conflicting role policy. Role policy shouldnt be an Excel spreadsheet. That's just plain embarassing for a rock star.
Role simplification: We need to work on reducing role proliferation and streamline what we have to be more reflective of the true business roles. We should include some definition of what exists withing EMS.
LONG TERM GOALS:
RFP for IAM Suite: We should look at what we have versus what's available in the industry. We'll need to get some scope definition in place, then we'll engage Gartner to craft a proper RFP. Once we've got that we'll send it to the major players to see who responds. I'm anticipating we'll evaluate IAM Suites from Oracle, Sun, Microsoft, and IBM, with the outside possibility of BMC. We should narrow that down to 2 vendors within 3-4 months and then do POC's with both. Based on the results of the POC, we'll select a vendor and engage Purchasing for the contract. Here's the timeline for the RFP:
December - January: Scope Definition. We'll need to work on getting the list of applications we have as an enterprise, then list what it is we have in terms of IAM support for all of them. Once we've got that we'll draft the RFP with Gartner.
February - March: Draft the RFP with Gartner. Vet it with the business. I'm anticipating 2-3 days with Gartner on site potentially.
April - May: Send out RFP and await responses.
June - August: Vendor on site meetings, demo's, and selection. I'm anticipating we'll make #1 and #2 offers by the end of August.
September - October: POC one and two.
November - December: Work with Purchasing to sign contracts. Begin to plan phased roll out.
IMPORTANT NOTE: An important option we have open to us throughout the RFP process is to pass on all vendors before or after the POC(s). The relative immaturity of the market, the relatively high prices, and the relative maturity of Apollo's IAM infrastructure by June of 2007 could suggest we pass on all vendors for 2007-2008.
The rationale behind the drive to select a single vendor or at minimum 2 partial vendors is to reduce the manpower needed to build and deliver identity and access management as well as to move away from something thats completely customized and labor intensive to own and operate. Our development resources should be able to get to a point where they are focusing on integration and delivering services to our fellow application developers in accordance with the service based model. This is very high level, very rewarding work. And then finally, when we're ready to tackle transitioning to a policy based model, our developers will very likely use a single vendors tool(s) to assist our business end users in defining and implementing their business policies in terms of identity and access management policies.
Presenting at IAM2: Next year, I want to be on stage at Gartner in Los Angeles talking about the best company with the best IAM team on the planet. I want to wow our fellow Gartner clients. I want them to base a case study on us. I want us to have to wear shades on stage that day, not because the lights are too bright, but because our FUTURE is SO bright we've got to wear shades.
